The roles in the below sequence include:
- User: Principal
- Agent: Web browser
- Resolver Core Client (Client): Web-based software GUI
- Resolver Core Web Services (Web Services): Service provider
- Identity Provider (IdP): ADFS, OneLogin, SiteMinder, CA, etc.
This sequence also assumes that:
- The user exists in Core and is a member of at least one organization;
- The user is not logged into Core;
- SSO SAML configuration has been imported using the IdP metadata and the primary email domain name; and
- The user is not logged into the IdP service.
SAML Sequence Diagram
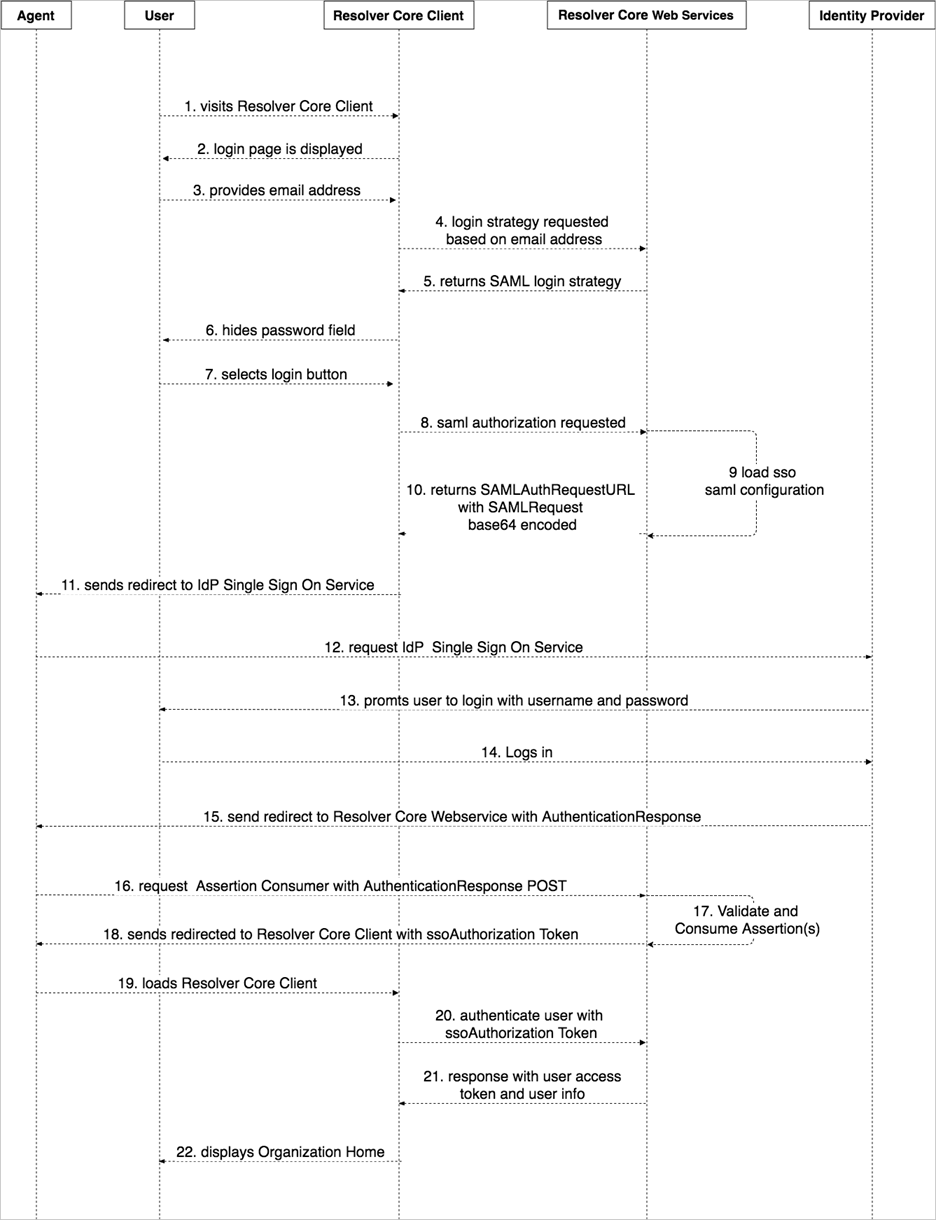 A sequence diagram showing the typical flow of SAML SSO authentication in Core.
A sequence diagram showing the typical flow of SAML SSO authentication in Core.
- User visits the Core client.
- Client displays the login page.
- User enters their email address.
- Client requests the authentication strategy using the provided email address. Web Services loads and asserts SSO SAML configuration using the domain of the domain of the email address.
- Web Services returns the authentication strategy to the Core Client.
- Client hides the password field and sets its state into SSO SAML authentication strategy.
- User clicks Login.
- Client requests an SSO SAML authorization using the provided email address.
- Web Services loads the SSO SAML configurations using the domain of the email address. The service uses the configuration to create a SAMLRequestAuthentication. The SAMLRequestAuthentication is a SAML 2.0 protocol XSD XML digitally signed deflated Base 64 encoded string.
- Web Services returns the request URL, which is the Single Sign On service URL with the SAMLrequest query PARAM containing the SAMLRequestAuthentication.
- Client sends a redirect to the Agent with the SAMLAuthentication.
- Agent requests the SSO service with the SAMLAuthentication.
- IdP service prompts the User to authenticate with their username and password.
- User logs in and authentication is successful.
- IdP sends a redirect to the Agent with the SAMLResponse.
- Agent redirects to the consumer service in Web Services with the SAMLResponse.
- Consumer service in Web Services validates the response and assertion, then retrieves the user identity from the assertion. The identity is the email address of the user who just logged in into the IdP. Web Services validates if the user exists. If the user exists and is active, an ssoAuthorization token will be created. This token is used by the Client to authenticate the user in Web Services and to obtain an access token.
- Web Services sends a redirect to the Agent with the ssoAuthorization token.
- Agent loads the Core client.
- Client authenticates the user into Web Services using the ssoAuthorization token.
- Web Services validates the token and authenticates the user into the Web Services. The Web Services then returns the user information and access token to the Client. The ssoAuthorization token is invalidated.
- Client displays the homepage of the organization.